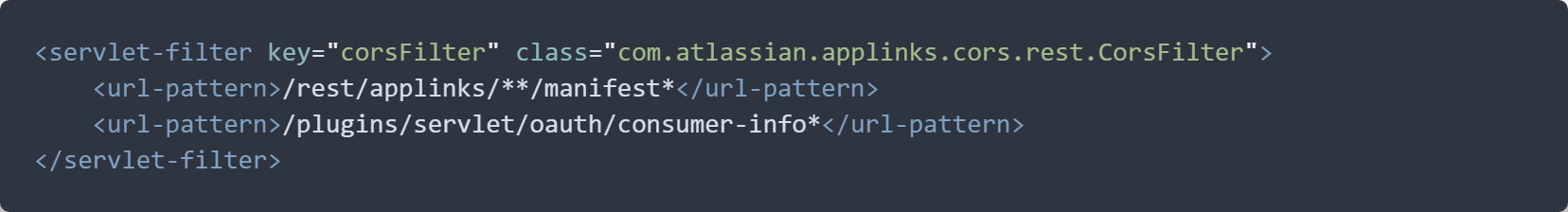
The Server version of Atlassian Confluence comes with a built-in plugin named applinks-cors, with the following declaration in file atlassian-plugin.xml:
The CorsFilter class is implemented as below:
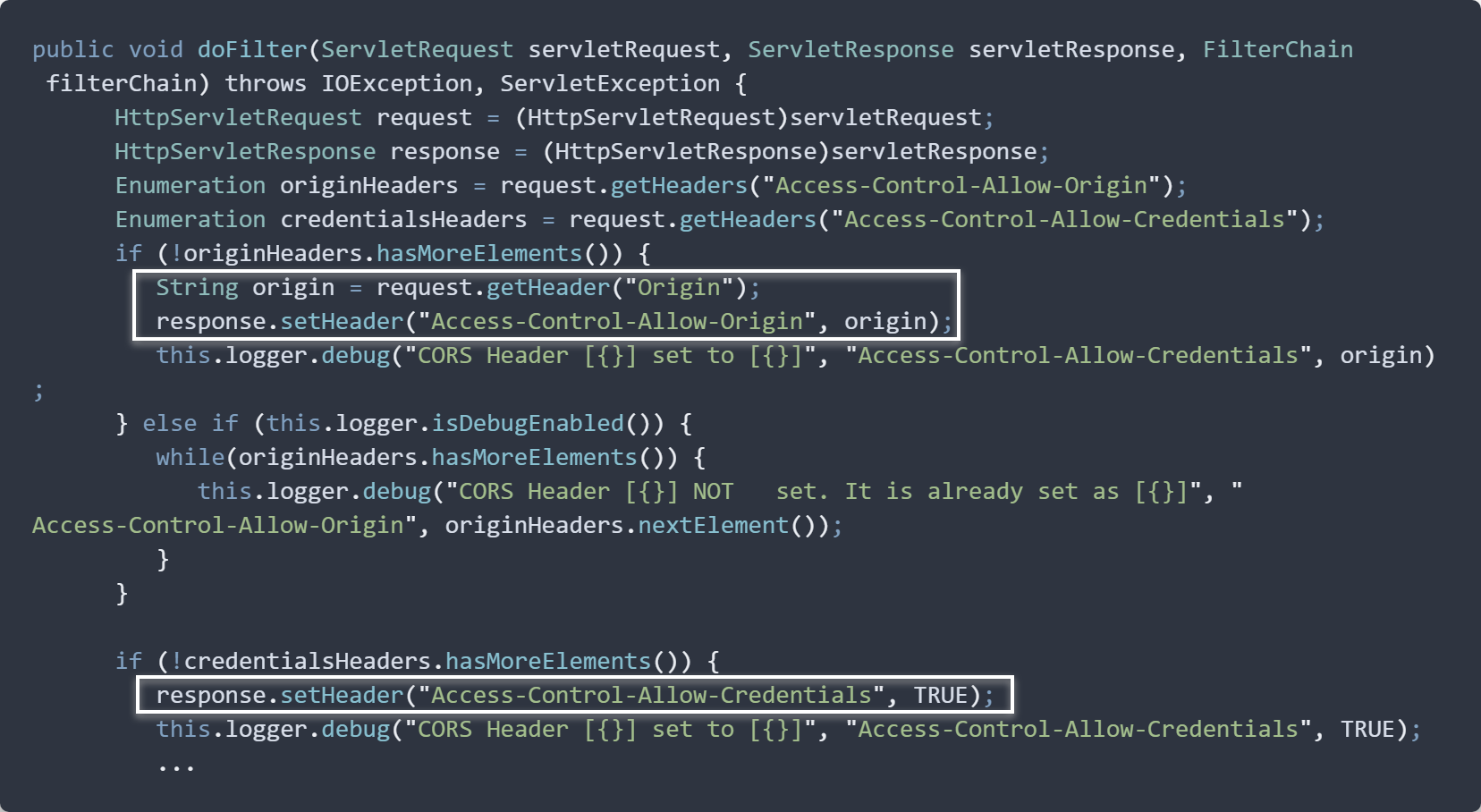
As we can see from the code, for all requests to URLs that match the defined patterns, Access-Control-Allow-Origin (ACAO) and Access-Control-Allow-Credentials (ACAC) headers will be added to the response. The important thing to note here is that the value of the ACAO header is taken from the Origin header of our request.
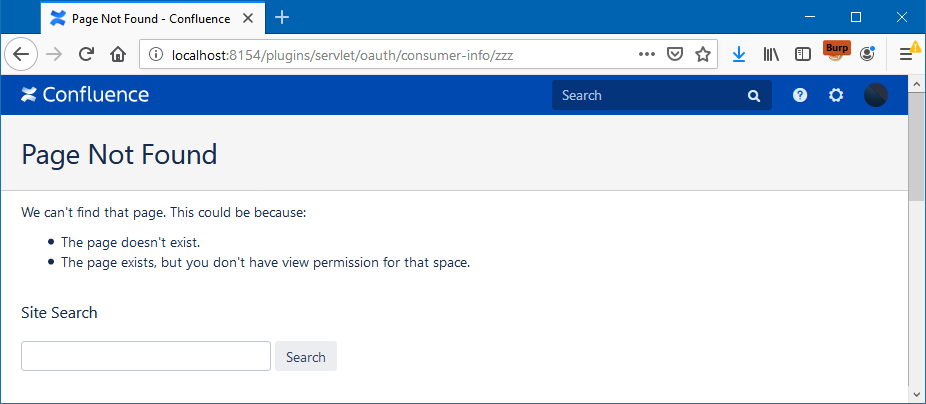
Besides, like many other web applications, accessing an invalid URL in Atlassian Confluence, for example, /plugins/servlet/oauth/consumer-info/zzz, will result in a 404 page:
In this case, since /plugins/servlet/oauth/consumer-info/zzz matches the /plugins/servlet/oauth/consumer-info* pattern, the ACAO & ACAC headers will be present in the response, allowing us to read the HTML content of the 404 page, which (un)fortunately, contains the CSRF token of the current user:
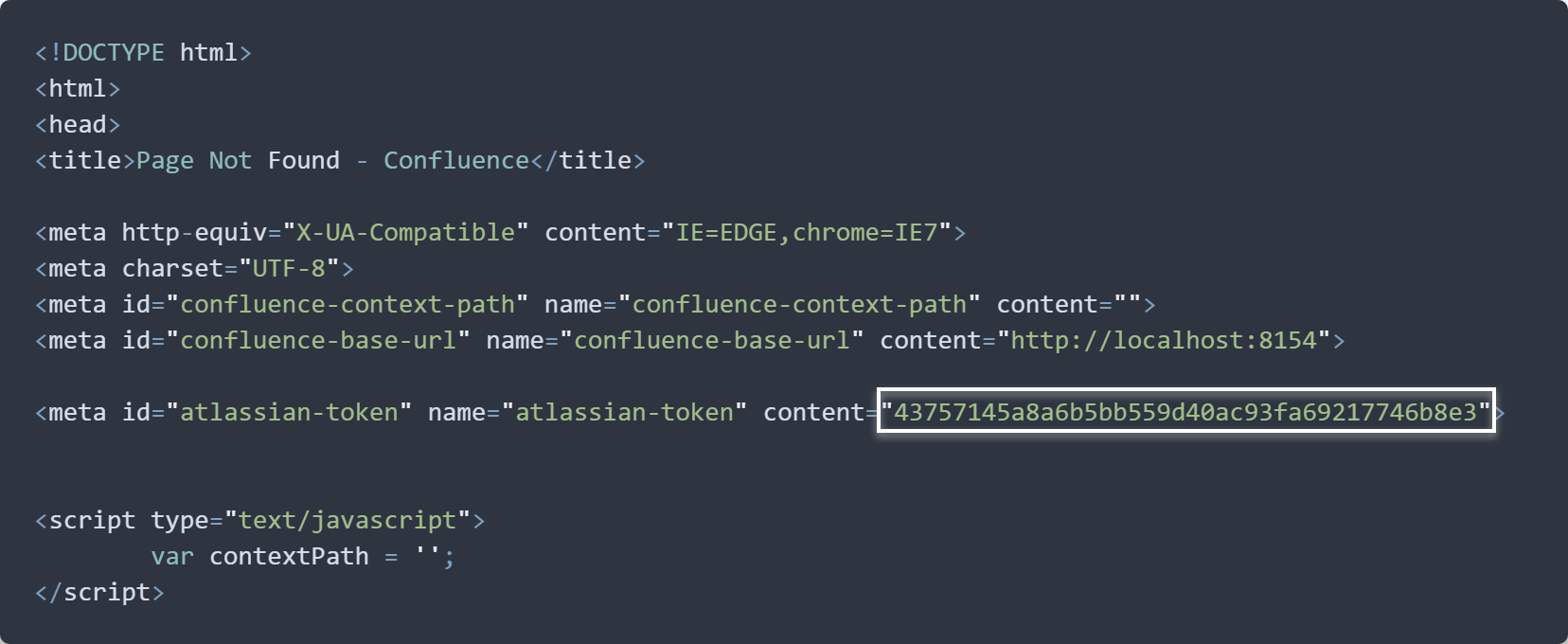
Therefore, a simple exploit strategy could be:
- Create a web page that when being visited by a victim, will send a request to the <victim-confluence-website>/plugins/servlet/oauth/consumer-info/ycs endpoint, then read its response to extract the CSRF token.
- Use the leaked token to bypass the CSRF protection.
In the situation where the Secure Administrator Session feature is disabled, or the victim is already in a Secure Administrator Session, the leaked CSRF token can be used to create a new administrator user, who has the ability to gain RCE on the target application via uploading a malicious plugin.
Note: Due to the new SameSite behavior implemented in recent versions of Chrome, most of CSRF vulnerabilities are now no longer exploitable (as the cookies/session of the victim will not be sent with cross-origin requests). If you want to reproduce the issue on your side, please use Firefox to avoid any trouble.
Fixed versions
- 6.13.9
- 6.6.17
- 7.0.3
- 7.1.0
Timeline
- 26 Apr 2019: Submission created on Bugcrowd.
- 12 Jul 2019: An incomplete fix was released.
- 17 Jul 2019: Another submission created (as suggested by Atlassian team).
- 15 Oct 2019: The issue got resolved (bounty: $1,800 x 2).
Xin gửi lời yêu thương đến 2 chuyên gia vigov và mov vì đã dành thời gian vàng ngọc xem trước bài.